Case Management
Alerts generate SIEM incidents. If the incident triggers an automated workflow, or playbook, a SOAR-based case is automatically created. Each case represents one or more incidents that make up a potential attack. A case is a series of events on a timeline, each event corresponds to an individual action within a playbook. Using cases can help you and your team track and understand what happened through the course of an automated investigation.
Cases are categorized according to whether they are a threat or a risk. You can also run SOAR Automation playbooks directly from a case or from a case's artifacts.
The external references or resources a playbook uses or accesses are termed artifacts. Out-of-the-box artifacts are:
-
Domain
-
Email
-
File
-
Generic Text
-
Host
-
IP Address
-
Hash Values
Each case has a dedicated owner, the individual who manages the case.
All cases are scored according to their potential severity.
-
Low 0 - 30
-
Medium 31 - 60
-
High 61 - 80
-
Critical 81 - 100
Working with Cases
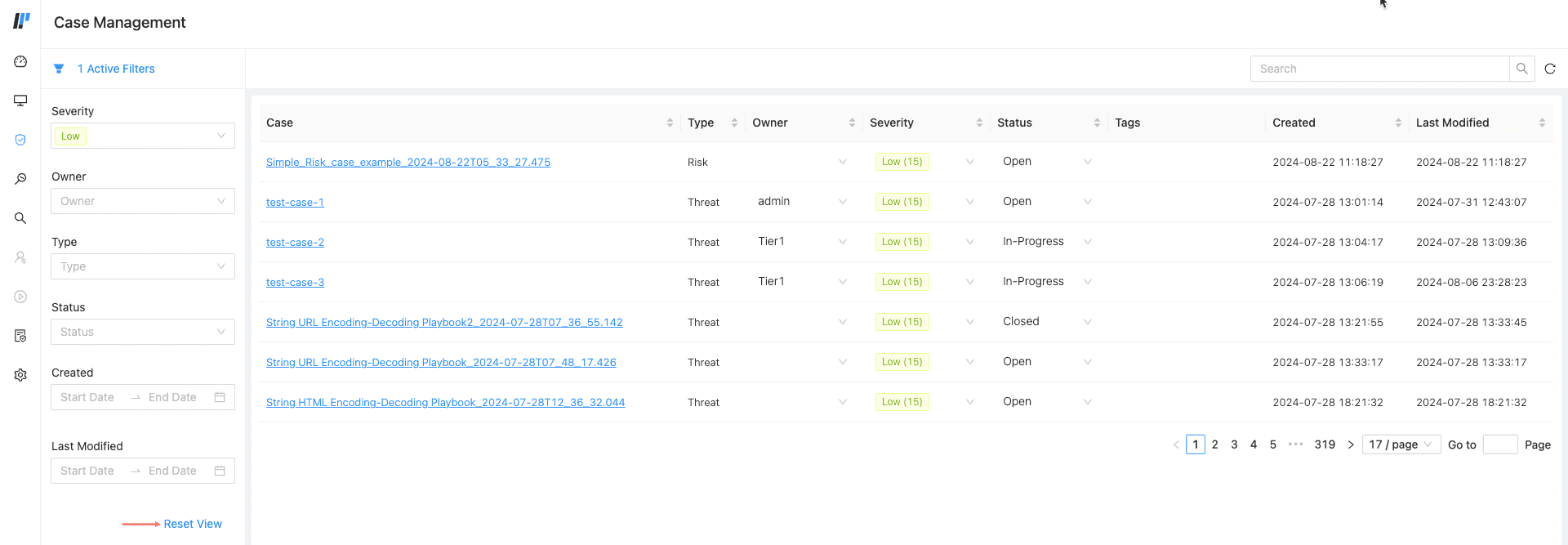
In the SIEM navigation bar, go to Incidents Cases and click Cases.
The list is an overview of all your organization’s cases. You can use the column titles to sort the list in ascending or descending order according to:
-
Owner
-
Severity
-
Status
-
Created date
-
Last Modified Dates
Enter criteria in Search to find specific cases or use Created from and Created to to search by date.
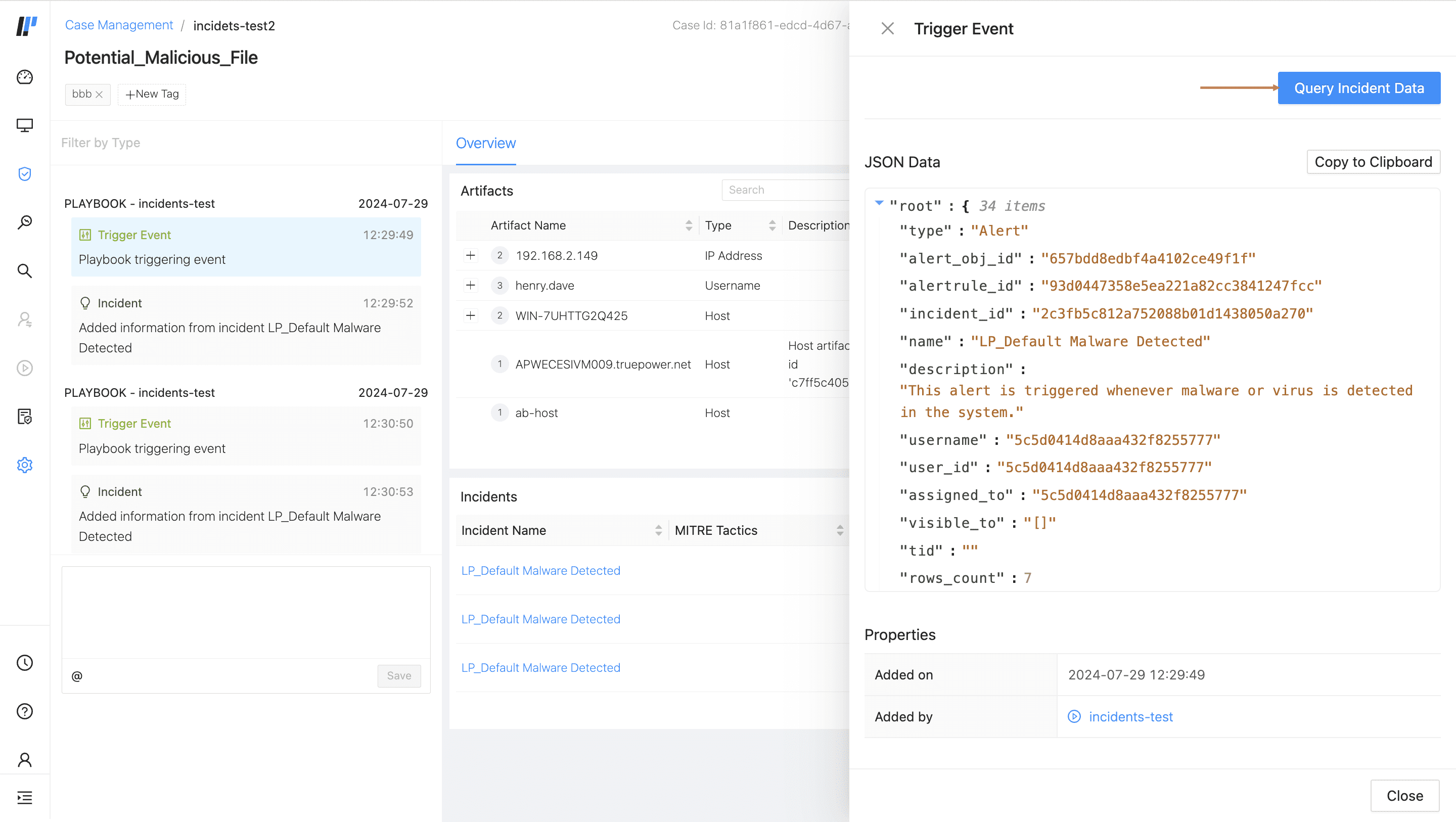
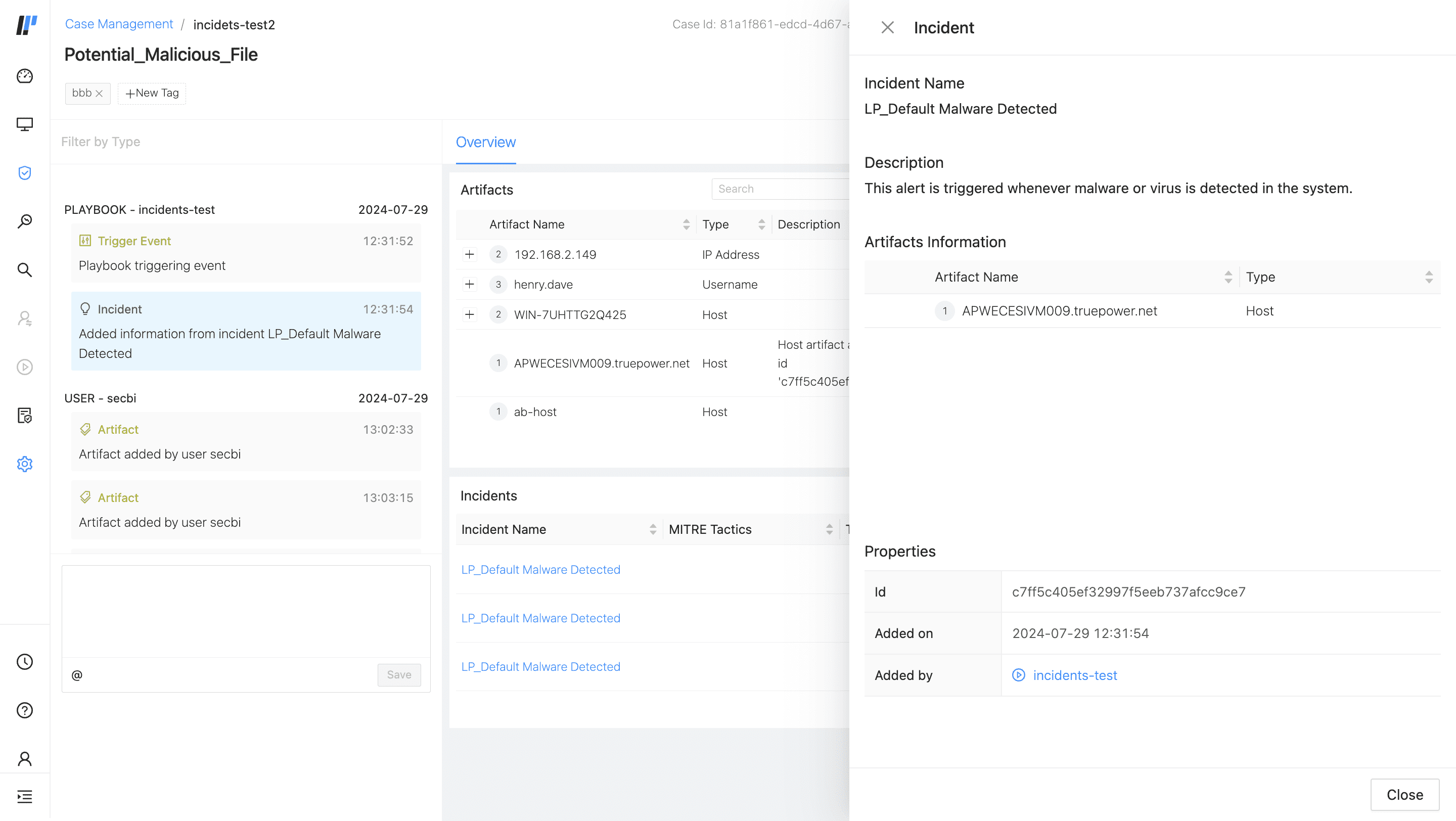
After you open a case, all of the events that make up the case are listed in a timeline on the left. These events help you understand what happened for each action of a playbook.
For example:
-
What was the trigger that started the playbook?
-
Who responded to a prompt action and what was their response?
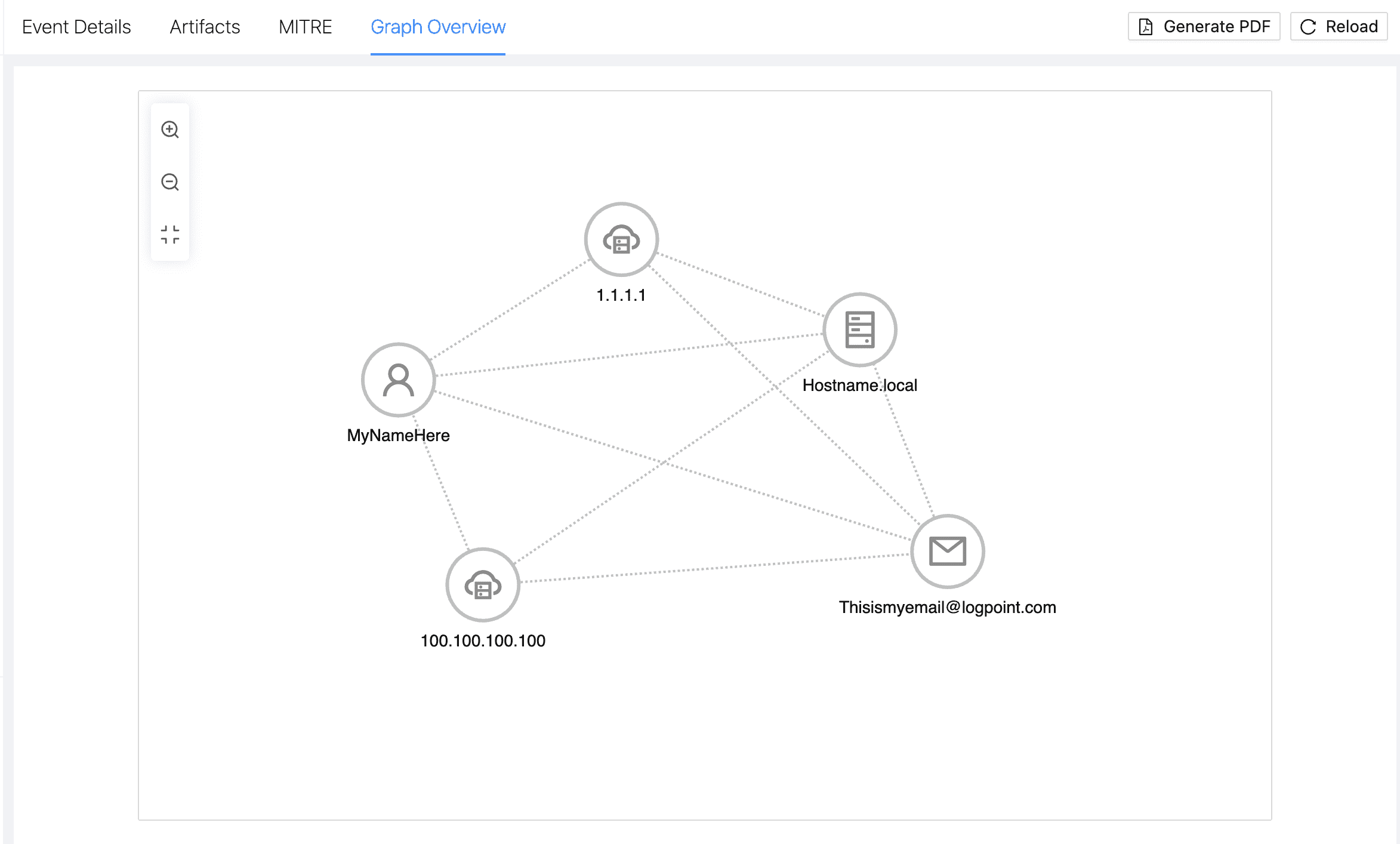
Graph Overview
Graph Overview is a visual representation of the connections among multiple events, incidents, and artifacts within a case.
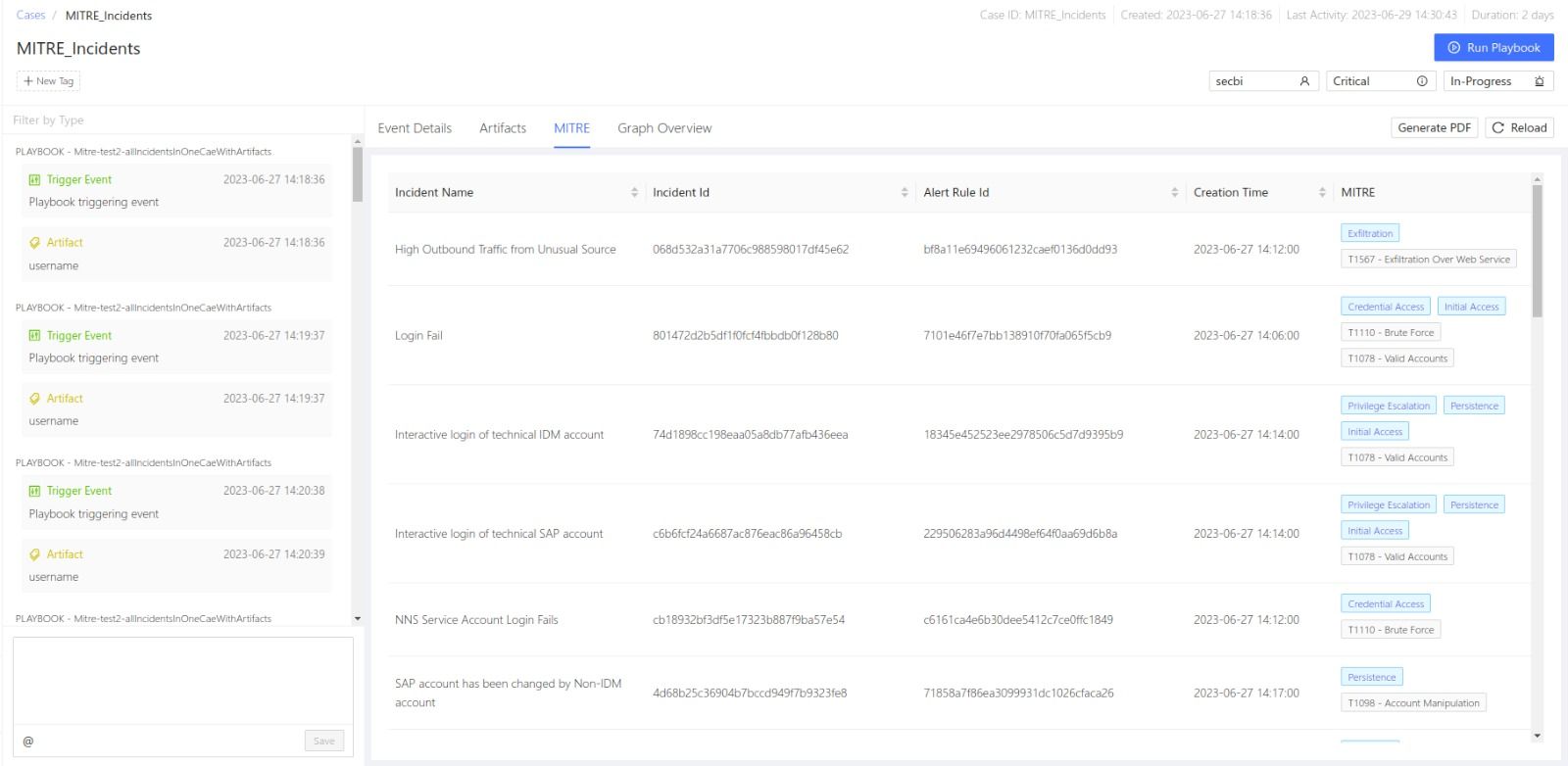
MITRE
MITRE displays the details of the incidents associated with a case and their MITRE tactics and techniques. To learn more about Logpoint MITRE ATT&CK Coverage, go to MITRE.
Events
Click on an event in the case, and the event’s details are listed on the right. Event details are the playbook’s action data. You can use event details as an audit log. If the playbook has a Prompt action, you can respond to it directly from the case timeline.
Cases have a Trigger Event for a specific incident, alert, or series of incidents or alerts resulted in an automated playbook running. You can use the logs of a Trigger Event to understand what triggered a playbook.
Artifacts are generated automatically when a playbook runs. It can also be helpful to add an artifact manually to add more details to the case.
1. Open the relevant case.
2. Select or click on an event in the timeline.
3. Click Artifacts at the top.
4. Next to the search field, click Add Artifact.
5. Select a type. The type you select determines what happens next.
6. Add the relevant data and external reference or file.
7. Click Save when you are done.
The external references or resources a playbook uses or accesses are termed artifacts. Out-of-the-box artifacts are:
-
Domain
-
Email
-
File
-
Generic Text
-
Host
-
IP Address
-
Hash Values
If you want to work with artifact types that aren't already included, add them manually.,
1. Open a relevant case
2. Click on an event in the timeline
3. Next to the search field, click Add Artifact.
4. In Add Artifact, go to Add New Artifact Type.
5. Enter the type’s name.
6. Click Add.
7. The new type is added to the list.
Add Search To Case
You can search the logs that triggered the playbook and then add the search results to the case. However, only 25 logs from a search can be saved to a case at a time.
1. Go to Investigation from the navigation bar and click Cases.
2. Click on a Case and click Trigger Event.
3. Click Search. You will be redirected to Logpoint Search.
4. Enter a query/queries to drill down on the Trigger Event Data.
5. Click Add Search To.
6. Click Case.
Run Playbooks
Run a playbook using one of the case’s artifacts. When you run a playbook, from the case or from an artifact, it is added as an event to the case so you can view the details of the playbook’s run.
1. Open a Case.
2. At the top right, click Run Playbook.
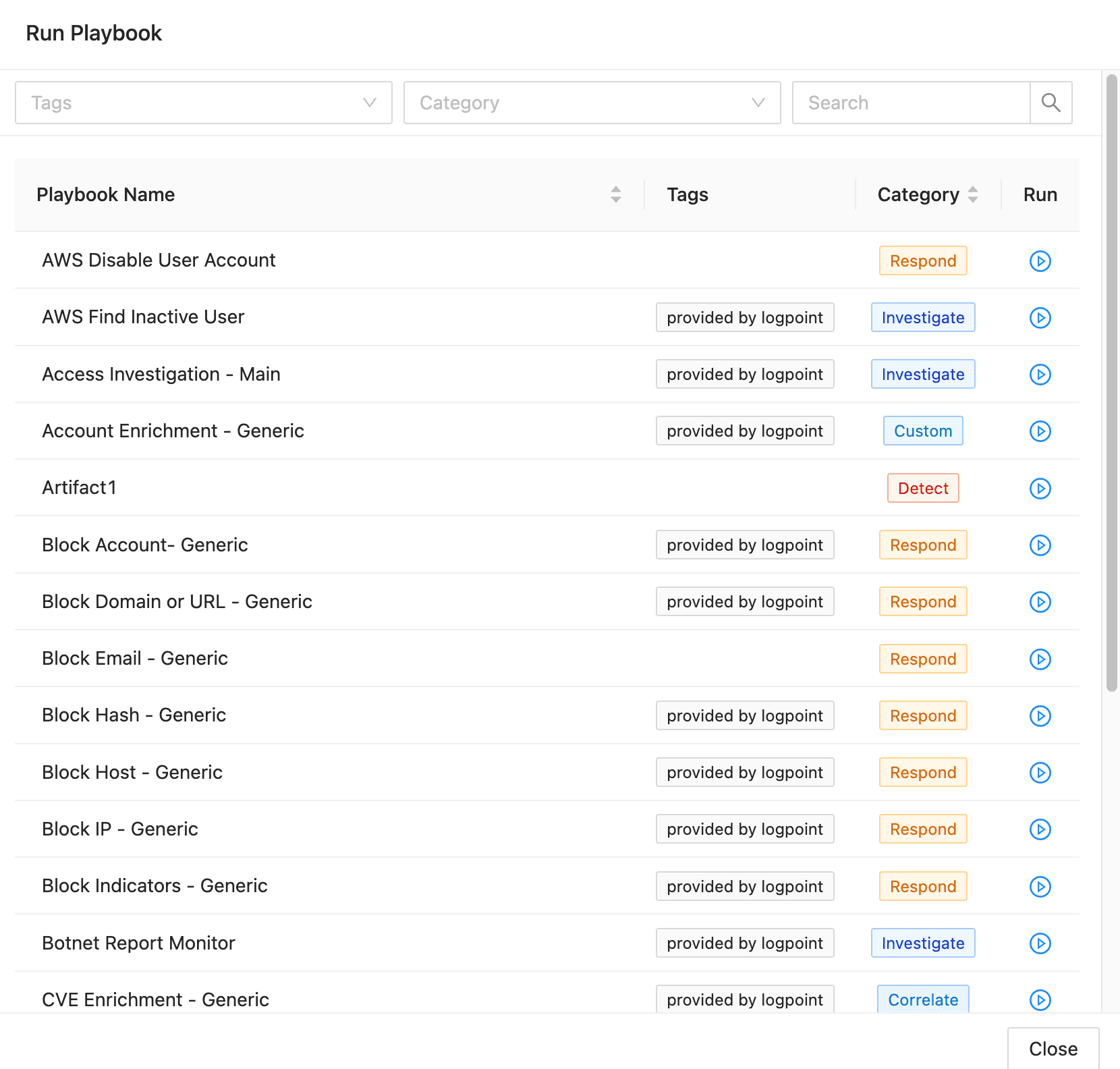
3. In the playbook list, find the relevant playbook.
3.1. You can filter the list using Tags and Categories.
4. Click Run.
5. Enter the relevant playbook parameters. Input Parameters correspond to Logpoint SIEM based data. These parameters are the data SOAR will retrieve and use from SIEM.
6. Click Run Playbook.
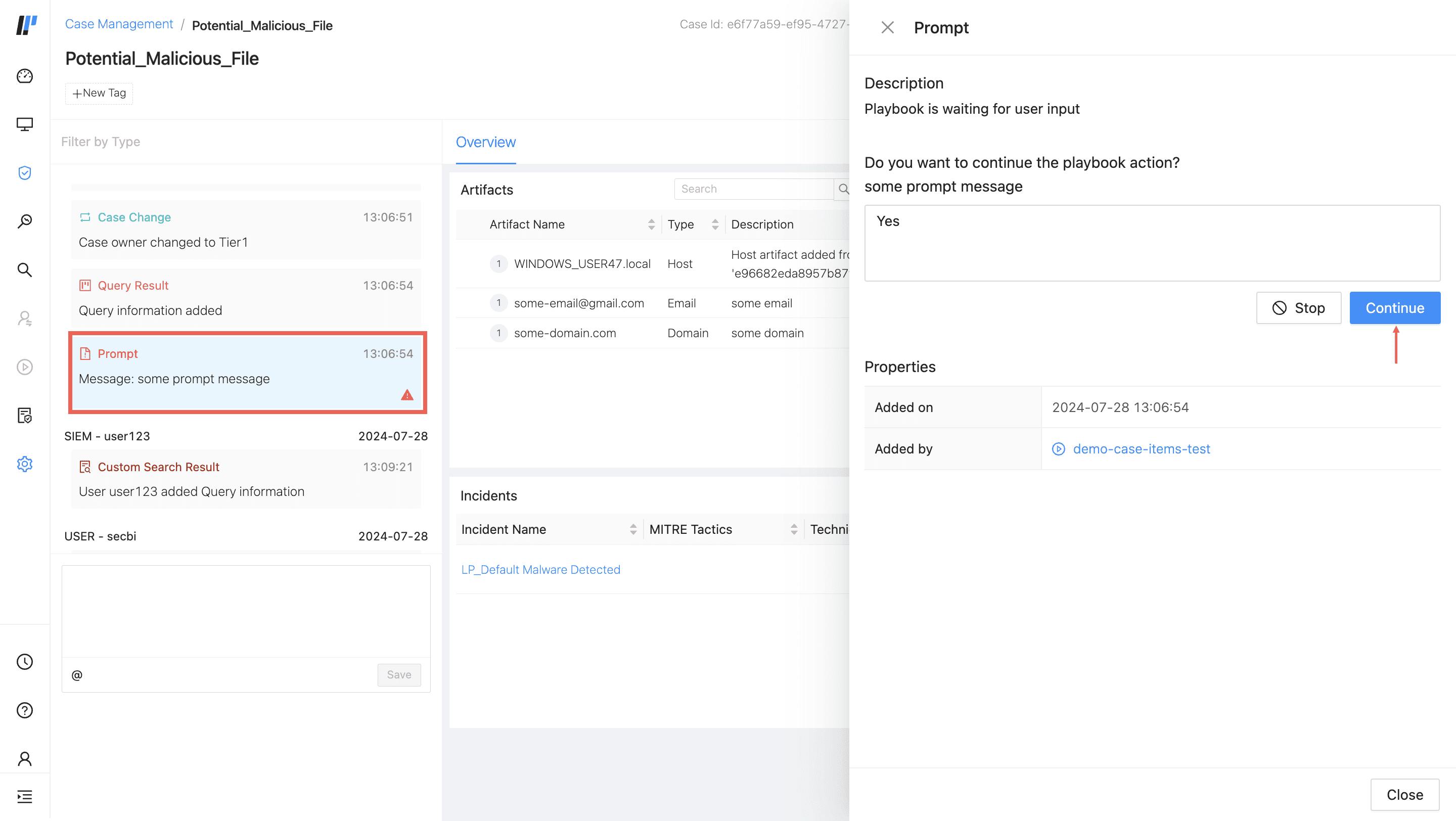
Prompt Playbook Action
Playbook Prompt Action sends a message to users that a manual action is required. The playbook stops running and only starts again after the prompt is responded to.
You can respond to the Prompt action block directly from the case timeline.
1. Go to Incidents Cases in the navigation bar and click Cases.
2. Search for the Case by applying the filters or entering the Case Name.
3. Inside your case timeline, click Prompt.
4. In Prompt, type your response.
5. Click Continue and Yes.
6. Click Close.
If you click Stop and No the playbook stops.
Tags
You can add tags to cases to help you group cases or find specific cases according to meaningful keywords. You add tags directly to an individual case.
1. Open a case
2. At the top of the case timeline, click + New Tag.
3. Enter the tag name
4. Click Enter.
The tag is added to the case. The case list also contains case tags; you can’t use the column to sort the list but can see the case’s tags.
Case Comments
You can add comments about the case to yourself or to someone else on your team. You can also tag another user in the comment.
Case comments are at the bottom of the case timeline. Add your comment directly and click Save. Your comment becomes part of the case timeline.
Case Ownership
Cases have owners, the individual who is managing the case. You can add an owner to a case or change the owner to someone else.
1. Open a case
2. At the top of event details, use the owner field to:
3. Select an owner from the drop-down.
4. Change the owner to a new one from the drop-down.
A new event is added to the case detailing who the owner is or who the owner is changed to.
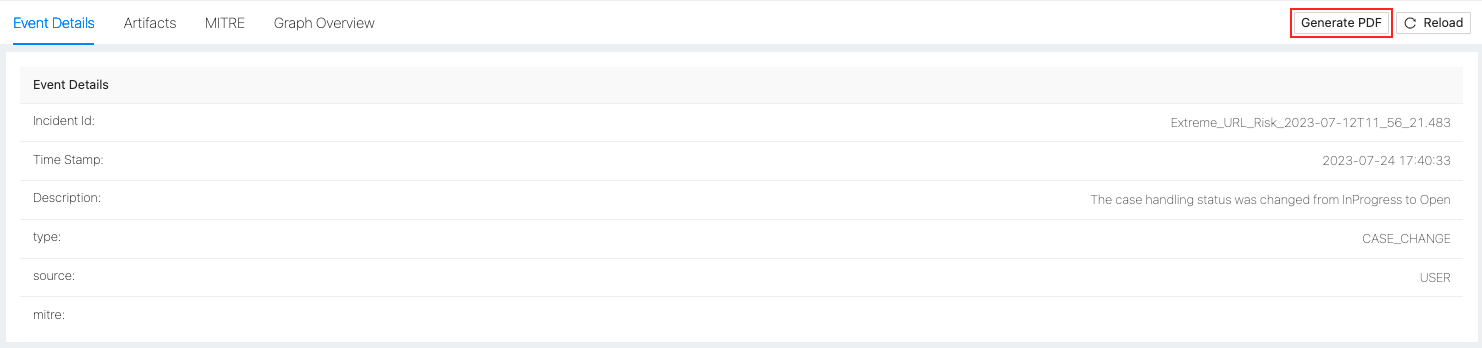
Case as a PDF
Click Generate PDF to export the case details in PDF.