Adjusting the time range and repo of alert rules is crucial for ensuring that alerts remain relevant and practical. For instance, to narrow the time range of an alert to focus on a specific window where suspicious activity was detected. By doing so, you can prioritize the most relevant data, ensuring quicker threat detection and response. Modifying the repo of an alert rule is essential when log sources change or when a broader or more specific dataset needs to be analyzed.
You can change the time range and repo for one, multiple or all alert rules.
Go to Settings >> Knowledge Base from the navigation bar and click Alert Rules.
Continue with ALL RULES or click the ALL RULES dropdown to select one of these filters: My Rules, Used Rules, or Shared Rules. You can now:
2.1. Search for a specific alert rule and select it.
2.2. Search for multiple alert rules and select them.
2.3. Select all alert rules.
Click the MORE dropdown.
Click Repo/TimeRange.
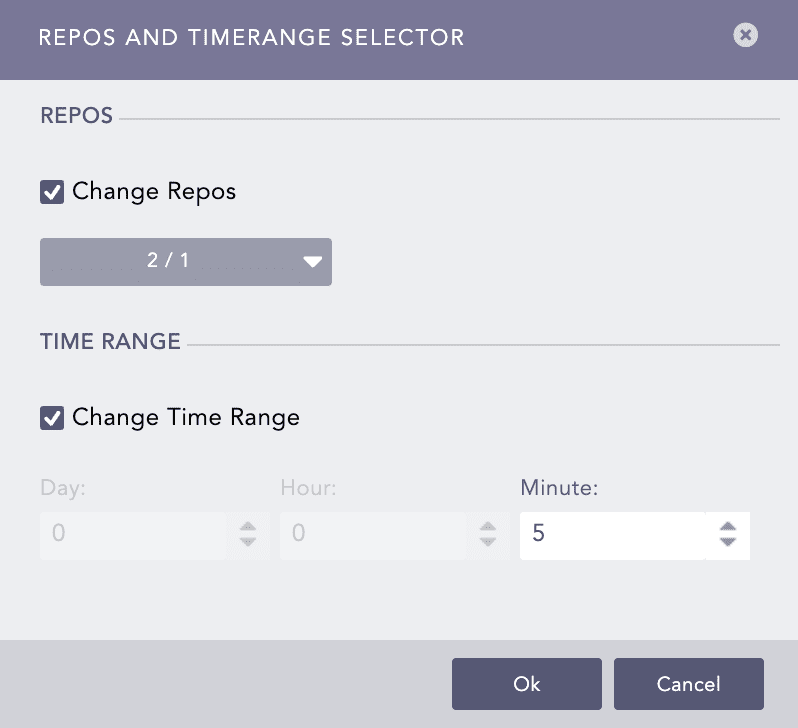
Select Change Repos and select the repo(s) from the dropdown.
Select Change Time Range and set the time range.
Click Ok.
Changing Repos and Time Range¶
Factors to Consider When Selecting a Time Range
Shorter time ranges reduce query load and improve performance.
Longer time ranges provide deeper insights but can increase processing time and generate more alerts.
When monitoring real-time threats, such as brute-force attacks or privilege escalation, 5–30 minutes is ideal for immediate detection.
Alerts based on high-frequency events, such as failed login attempts, must use a shorter time range to prevent excessive alerts and focus on the latest activity.
Alerts for low-frequency events, such as unauthorized admin access, benefit from a longer time range to capture meaningful patterns.
During an active security investigation, you need to adjust the time range dynamically to analyze specific attack windows.
Factors to Consider When Selecting a Repo
The repo must contain logs that match the event type being monitored. For example, an alert for failed login attempts must be assigned to a repo containing authentication logs, like Windows Event Logs, Active Directory logs or VPN logs.
If an alert rule applies to multiple data sources, select a repo that includes all relevant logs to ensure no critical logs are missed.
Some alerts must be assigned to specific repos to meet compliance requirements, such as PCI DSS, GDPR or ISO 27001.
If an alert requires correlation across different log sources, such as firewall, endpoint, and Logpoint logs, ensure the repo contains the necessary log types.
Large repos with extensive logs can slow down query performance.
We are glad this guide helped.
Please don't include any personal information in your comment
Contact Support