Alert Notification notifies you when a alert rule is triggered. You can set it to send notification every time the alert rule is triggered or send it manually from Incident Actions. You can set up alert rules and configure how to be notified. It ensures timely and appropriate actions, helps prevent data breaches, minimizes downtime, and enhances overall security.
You can set alert notifications for one, multiple or all alert rules listed under the All Rules, My Rules, Used Rules and Shared Rules filters.
Go to Settings >> Knowledge Base from the navigation bar and click Alert Rules.
Continue with ALL RULES or click the ALL RULES dropdown to select one of these filters: My Rules, Used Rules, or Shared Rules. You can now:
2.1. Search for a specific alert rule and click the Setup Notification ( ) icon from the Actions of it.
) icon from the Actions of it.
2.2. Search for multiple alert rules and select them.
2.3. Select all alert rules.
Click the MORE dropdown.
Select Setup Notifications of Selected Alert Rules.
For step b and c, select Overwrite existing notifications in all the notifications.
Set up Email, HTTP, IncMan, SSH, SMS and SNMP alert notifications via:
Email notification allow you to receive alerts directly in your inbox. When an alert rule is triggered, an email containing the event’s details is sent to the specified email addresses. You must configure the SMTP service before sending email notifications.
Click Email Notification and select Notify via email.
In Notification Trigger:
Select Automatic to send a notification every time the alert rule is triggered.
Select Manual to manually send the notification from the Incident Actions.
Enter valid email address(es) in Emails.
Enter a Subject. Logpoint supports various Jinja commands for alert rules. You can use the Jinja placeholders as templates to customize the output of your subject. You can write them in the Subject field as:
Logs from {{rows[0].col_type}} on date {{rows[0].col_ts|datetime}}
To learn more about which Jinja commands you can use for the Subject and Message fields, go to Logpoint Reserved Jinja Placeholders and for the examples, go to Jinja Templates.
Select Toggle Simple View to enable or disable the advanced text editor.
Select Disable Search Link to remove the search link in the email. The search link redirects to the search page of the Logpoint machine from which the email notification is configured.
Enter a Message.
Set the Threshold.
If you do not want to include the Logpoint logo in the email, deselect Enable Logo and click Save.
Browse for the image in the JPG/JPEG format if you want to provide a custom logo. The maximum dimension for the custom logo is 600*400.
Click Save.
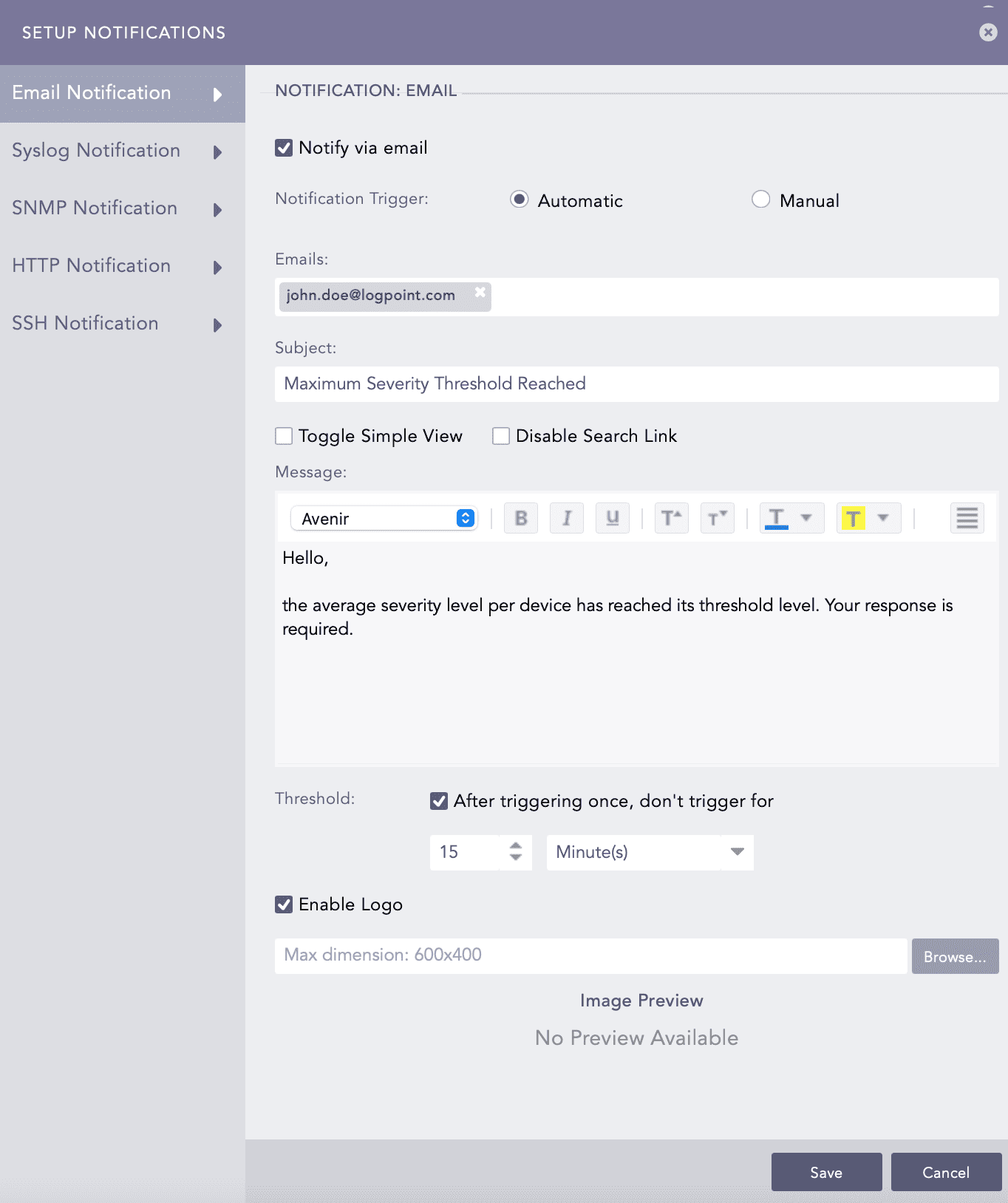
Setting Email Notification¶
Logpoint can send an HTTP POST or GET request to a specified URL when an alert rule is triggered.
Click HTTP Notification and select Notify via HTTP.
Under Notification Trigger:
Select Automatic to send a notification every time the alert rule is triggered.
Select Manual to manually send the notification from the Incident Actions.
Select Protocol as HTTP or HTTPS.
Enter either a valid IP address or domain name in the Base URL field.
Select a Request Type from the drop-down.
Enter a Query String. You can use the Jinja commands in the Query String and Body fields. You need to input JSON string in the Body field. To learn more about which Jinja commands you can use for the Body field, go to Logpoint Reserved Jinja Placeholders and for the examples, go to Jinja Templates.
You can write them in query as:
user='admin'&count={{rows_count}}
Select an authentication Header type.
If you select Basic Auth, enter the Key and Password.
If you select API Token, enter the Key and Value.
If you select Bearer Token, enter the Key.
Enter a template for the Body of the HTTP notification in Jinja format.
You can enter the template only for the POST, PUT, and PATCH request methods.
Set the Threshold.
Click Finish.
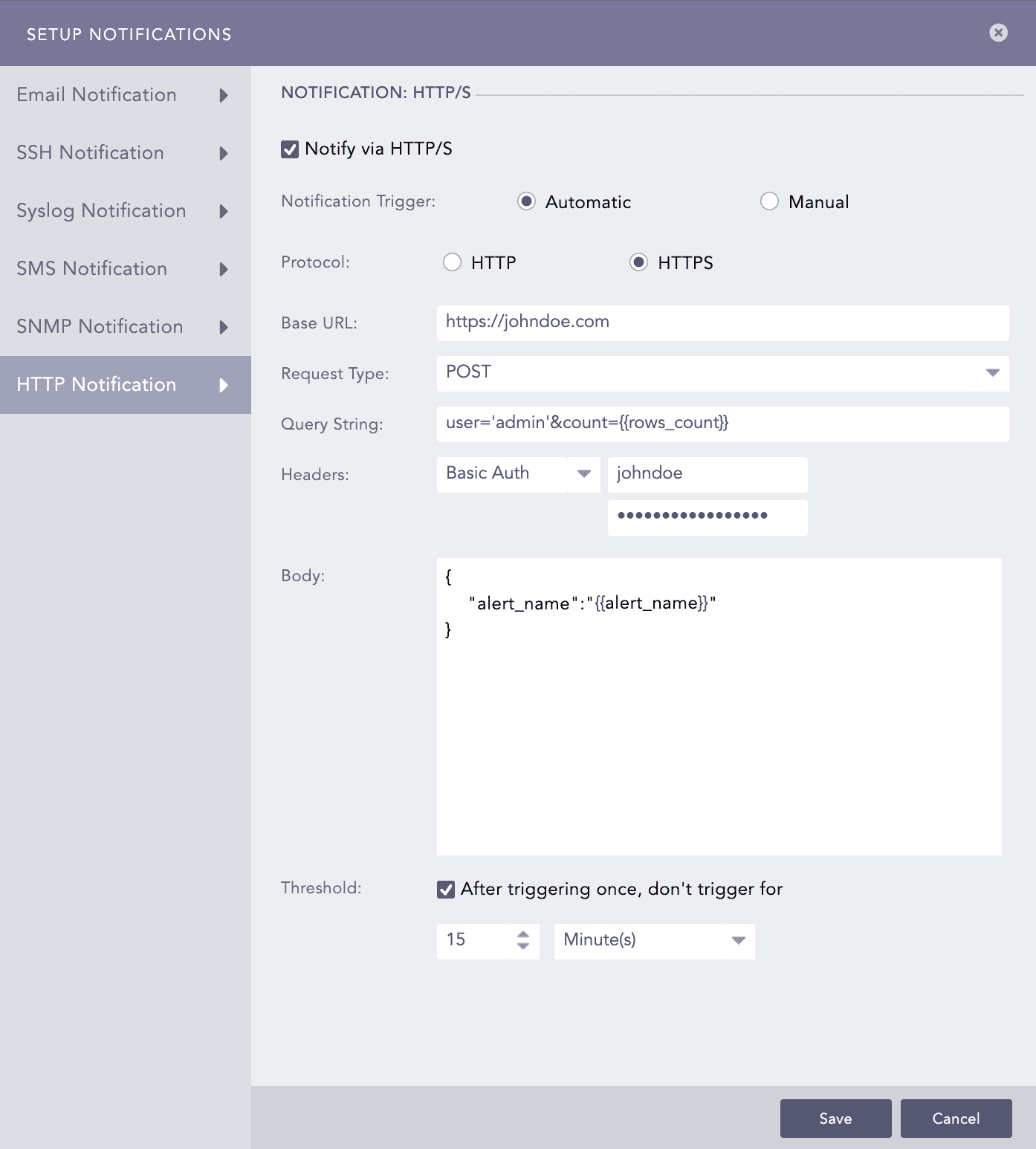
Setting HTTP Notification¶
You can use IncMan notification to escalate critical events directly to IncMan, ensuring that incidents are investigated and resolved with minimal delay.
Click IncMan Notification and select Notify via IncMan.
Select Alert Type, Severity, Facility and **Threshold**from the dropdown.
Select Threshold and set the trigger interval in minutes. The threshold determines how many times an event must occur before triggering an alert, while the interval defines the time gap for evaluating the threshold.
Click Save.
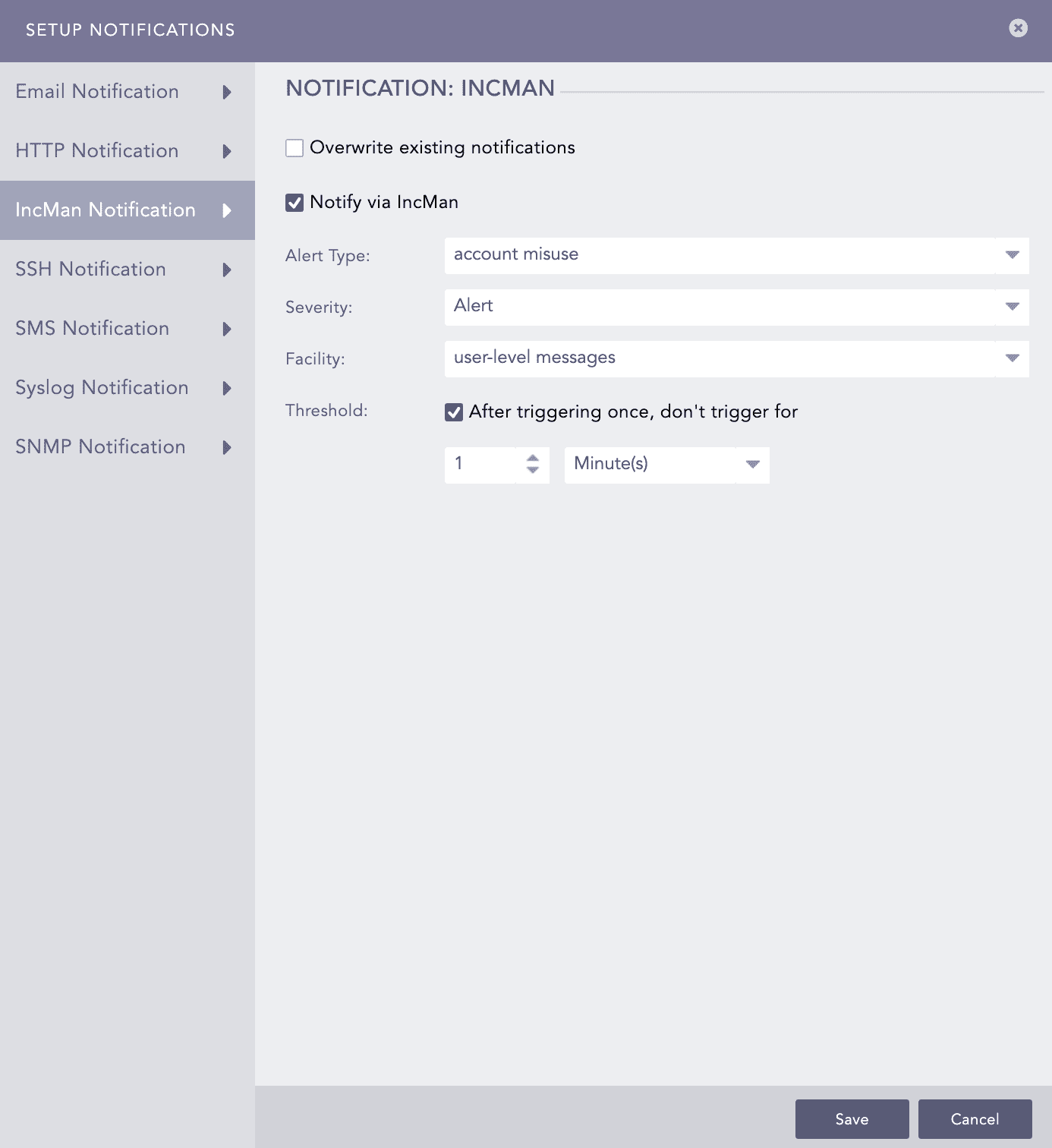
Setting IncMan Notification¶
You can configure alert notification to execute a command or script on a remote server via SSH based on the alert information when an alert is triggered.
Click SSH Notification and select Notify via SSH.
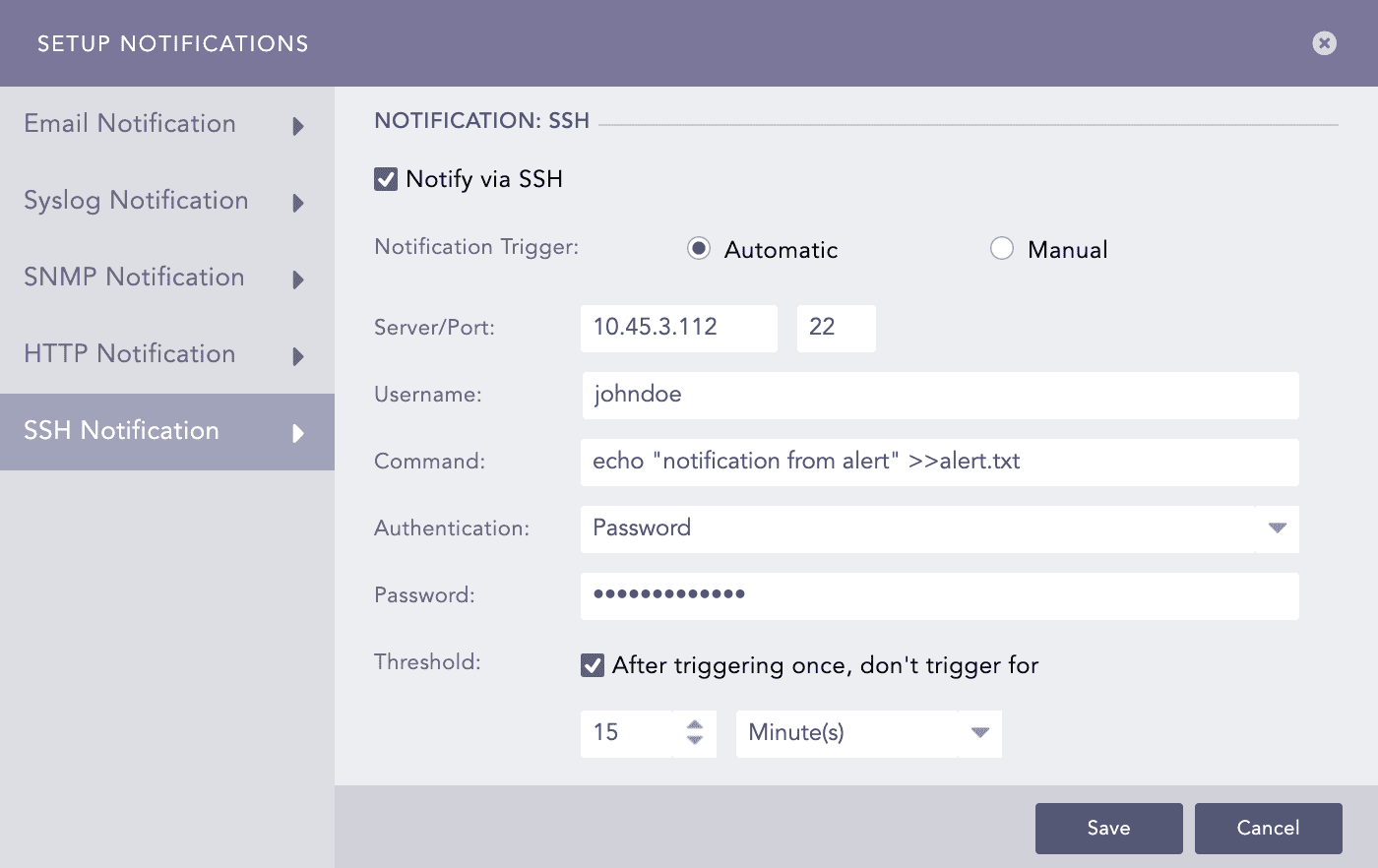
Setting SSH Notification¶
In Notification Trigger:
Select Automatic to send a notification every time the alert rule is triggered.
Select Manual to manually send the notification from the Incident Actions.
Enter a Server address and a Port number.
Enter a Username for the user in the destination server.
Enter a Command you want to execute when the alert rule is fired. Make sure that the command is a valid bash command and is executable. You can use the Jinja commands in the Command field. To learn more about which Jinja commands you can use for the Command field, go to Logpoint Reserved Jinja Placeholders and for the examples, go to Jinja Templates.
Select the required mode of Authentication: Password or SSH Certificate.
If you select Password, enter a passkey in the Password tab.
If you select SSH Certificate, select the Certificate type: System Certificate or User Certificate. The SSH Certificate key is automatically generated. You must add the key to the authorized keys at ~/.ssh/authorized_keys in your system.
If you select System Certificate, Logpoint uses system-specific certificate for authentication.
If you select User Certificate, Logpoint uses individual user-specific certificate for authentication.
It is important for you to remember the password or the SSH certificate key as it is required later for user-validation.
Set the Threshold.
Click Finish.
SMS notifications enable users to receive alerts on their mobile devices. Before configuring SMS notification, SMSC server must be accessible from Logpoint.
Click SMS Notification and select Notify via SMS.
In Notification Trigger:
Select Automatic to send an sms notification every time the alert rule is triggered.
Select Manual to manually send the sms notification from the Incident Actions.
Enter SMSC Server/Port. The SMSC server supports both hostname and IP address.
Enter Username, Password, and Sender ID of the server.
In Receivers, enter the phone numbers of the receivers. You can also include country code if necessary.
In Body, enter the SMS message. You can also use Jinja commands. To learn more about which Jinja commands you can use for the Body field, go to Logpoint Reserved Jinja Placeholders and for the examples, go to Jinja Templates.
Set the Threshold time to trigger the SMS notification after enabling it.
Click Save.
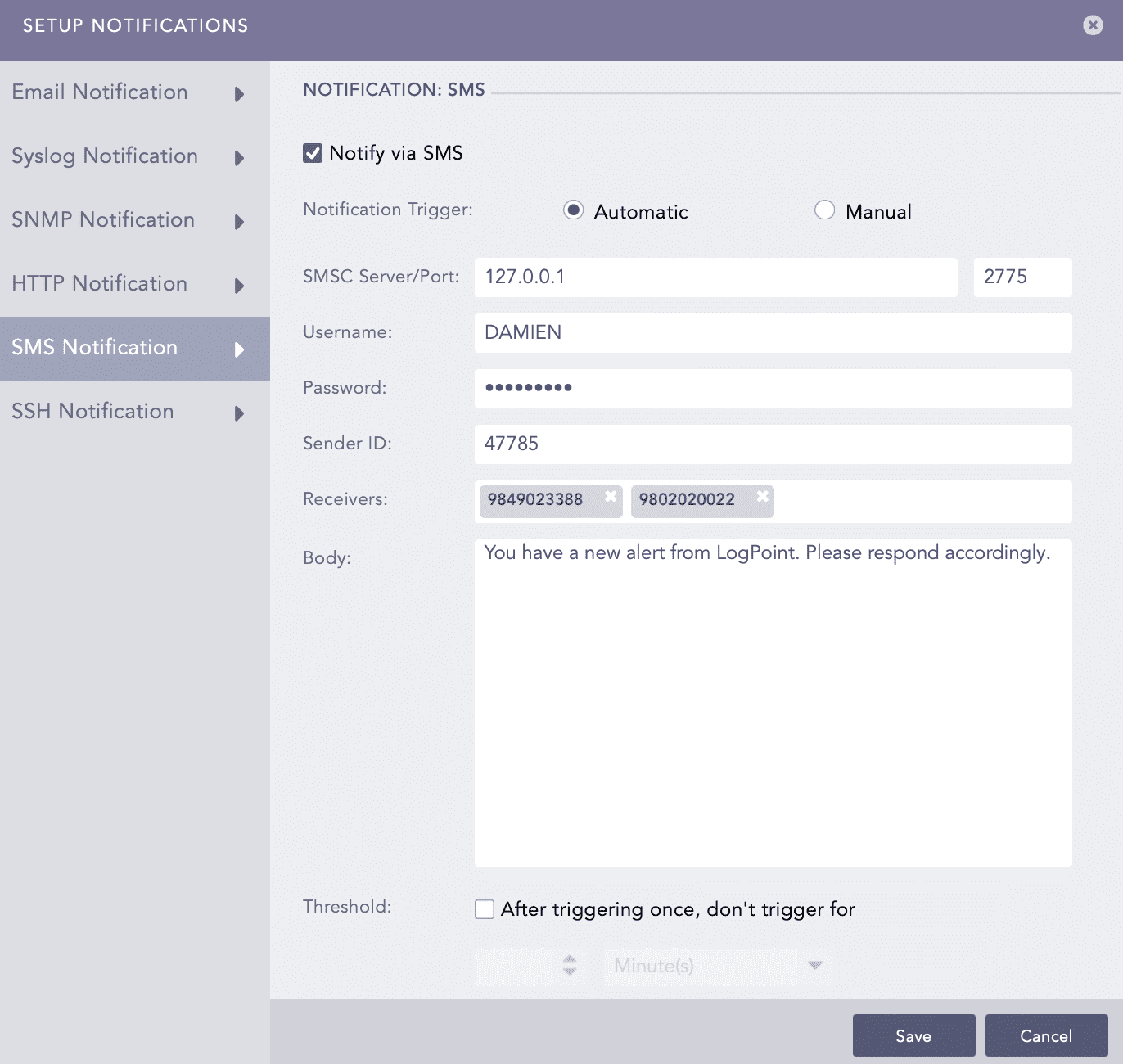
Setting SMS Notification¶
When an alert rule is triggered, Logpoint sends the alert details to the Syslog server, where it can be stored, analyzed, or forwarded.
Click Syslog Notification and select Notify via Syslog.
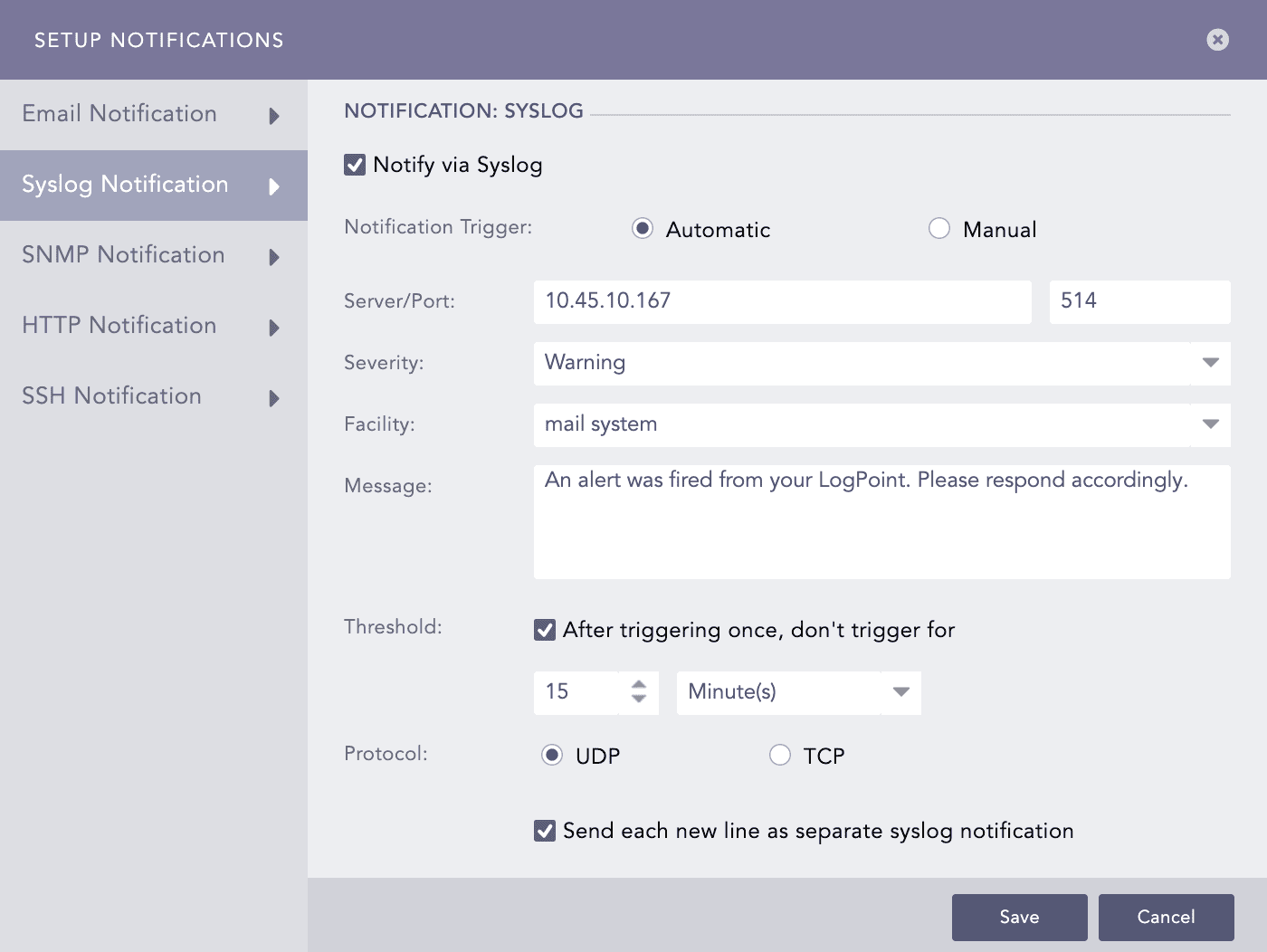
Setting Syslog Notification¶
In Notification Trigger:
Select Automatic to send a notification every time the alert rule is triggered.
Select Manual to manually send the notification from the Incident Actions.
Enter the IP Address and the Port number for the syslog receiver in the Server/Port textboxes.
Select the level of Severity and Facility from the drop-downs.
Enter a Message that provides the information about the event. You can use the Jinja template to construct a message that extracts specific information about the event. To learn more about which Jinja commands you can use for the Message field, go to Logpoint Reserved Jinja Placeholders and for the examples, go to Jinja Templates.
Set the Threshold.
Select the UDP or the TCP protocol to send the Syslog Notification.
If you use UDP, the log message may be dropped or it may arrive out of order.
If you use TCP, the log message arrives without being dropped and in order.
Select the Send each new line as separate syslog notification checkbox to generate one syslog message for each log message in the search results. If you do not select it, all the messages within the chosen time range of the incident are compressed into one syslog message in the search results.
The Send each new line as separate syslog notification option is useful only if the Message textbox contains a Jinja template with a for loop.
SMTP and SSH services can have the Jinja2 syntax as a message or a command.
For SMTP, you can include the jinja2 syntax in the Message textbox to deliver more information about the alert rule fired. Using jinja2, you can explain the incident in an elaborate way and can fetch individual data while the alert is fired.
{{rows_count}} returns the count of the row.
{{rows}} returns the list of rows returned from a search query.
{{rows}} returns a list in a machine-readable format which is difficult to read. Use filter functions with your Jinja syntax for a readable list. The available filter functions are as follows:
readable
This command has its effect according to the query provided in alert; for plain search, it returns the result in a list whereas for queries with chart/time chart it displays the output in a tabular form. Use this filter as:
{{ rows | readable }}
date
You can convert the fields containing UNIX timestamp in year/month/day format. Use this filter as:
{% for row in rows %}
{{row.col_ts | date}}
{% endfor %}
time
This command converts the UNIX timestamp and displays the time in the format hour:minute:second. Use this filter as:
{% for row in rows %}
{{row.log_ts | time}}
{% endfor %}
datetime
You can use this syntax to convert datetime from UNIX timestamp. The result is displayed in the year/month/day hour:minute:second format. Use this filter as:
{% for row in rows %}
{{row.log_ts | datetime}}
{% endfor %}
You can also provide additional parameters to specify the required format.
Syntax to specify the format:
datetime (format_string, timezone)
For example:
{% for row in rows %}
{{row.log_ts | datetime ("%d %m %Y %H:%M:%S", "Asia/Kathmandu")}}
{% endfor %}
Iteration Through Values
You can iterate through the values returned from {{rows}}, use loops to view the items returned.
For query
error|chart count() by device_ip
You can use the following syntax in the message:
{%for row in rows%}
{{row.device_ip}}
{%endfor%}
This outputs the device_ip for every list returned by rows.
For Simple Search
You can use the readable function in case of simple search queries. If the parameters returned from the search queries contain UNIX timestamps, then you can use the date, time or datetime to convert them into readable form.
For searches with chart/timechart
You can use the readable function to clearly understand the values returned from the {{rows}}. If grouping functions used in the search query return the parameters containing UNIX timestamps, then you can convert filter functions date, time, and datetime into readable form. All the filter functions except the readable should be used in loops.
When using a timechart in a search query, the timechart function is considered an aggregation function because it returns a UNIX timestamp for the search results. Therefore, when you use timechart count(), the count() part is the primary aggregation function. You can use the jinja syntax as:
{%for row in rows%} {{row.device_ip}} {{row.colx}} {%endfor%}where colx is the displacement count of timechart function.
Timechart can be represented with the timestamp so you can write jinja syntax as:
{%for row in rows%} {{row.device_ip}} {{row.timestamp}} {%endfor%}
Order of Operations
For query:
| chart count(), max(port) as MAX, min(sev,sev>>3) by device_ip,
source_address, step(destination_port,100)
Use the following jinja syntax:
{%for row in rows%}
{{row.device_ip}}
{{row.source_address}}
{{row.MAX}}
{%endfor%}
The grouping function is written as it is in the query making device_ip and source_address same in query and syntax. Aggregation functions can be mentioned with their aliases; max(port) in the search query is denoted as MAX in jinja syntax. You can use the position of the functions and name them accordingly.
For the query above:
The numbering starts from the first grouping function and goes from left to right as:
device_ip= col1 source_address=col2 step(destination_port,100)=col3The complex functions such as step(destination_port,100) can not be used directly in jinja, the only way to use them is by using displacement count.
Example:
{%for row in rows%} {{row.device_ip}} {{row.col3}} {%endfor%}Once the grouping functions are done with naming, the order moves to the beginning of the aggregation function and the numbering goes as:
max(field)=col4 min(sev, sev>>3)=col5If aliases are used for aggregation functions, they can be written directly in jinja syntax. In the example above, for max(port) the Jinja syntax can be written as:
{%for row in rows%} {{row.MAX}} {%endfor%}
For SSH in the SSH command, you can use the following jinja2 keywords:
Keyword |
Syntax Definition |
|---|---|
{{rows_count}} |
Number of rows |
{{alert_name}} |
Name of the alert |
{{correlation_name}} |
Name of the correlation |
{{detection_timestamp}} |
Detection timestamp |
{{risk_level}} |
Risk level |
For example:
For the query User Login, you can use the command:
``echo alert with log count ={{rows_count}} with risk_level= {{risk_level}} >> /tmp/login_alert.txt``
After the alert is fired, login_alert text is created at destination location with the number of rows and the risk level of alert.
Logpoint sends an alert to an SNMP-enabled network management system when an alert rule is triggered.
Click SNMP Notification and select Notify via SNMP Traps.
In Notification Trigger:
Select Automatic to send a notification every time the alert rule is triggered.
Select Manual to manually send the notification from the Incident Actions.
Enter the trap receiver’s IP address and the Port number.
Enter a valid SNMP trap or Enterprise specific OID (Object Identifier) in the dotted decimal format. Make sure to not use the OID with a leading dot.
Select SNMPv2c or SNMPv3 according to the security level you require.
The notification settings change according to the version you pick.
For SNMPv2c configuration
Enter the name of the Agent that sends the SNMP trap.
Enter a passphrase in the Community String. The passphrase should be recognizable by the manager.
Enter the OID’s corresponding value in the Message.
For SNMPv3c configuration
Enter the Username.
Enter the Authorization Key and Private Key. You can select whether to Show or Hide your key.
In the Message field, enter the OID’s corresponding value. You can use the Jinja commands in the Message field. To learn more about which Jinja commands you can use for the Message field, go to Logpoint Reserved Jinja Placeholders and for the examples, go to Jinja Templates.
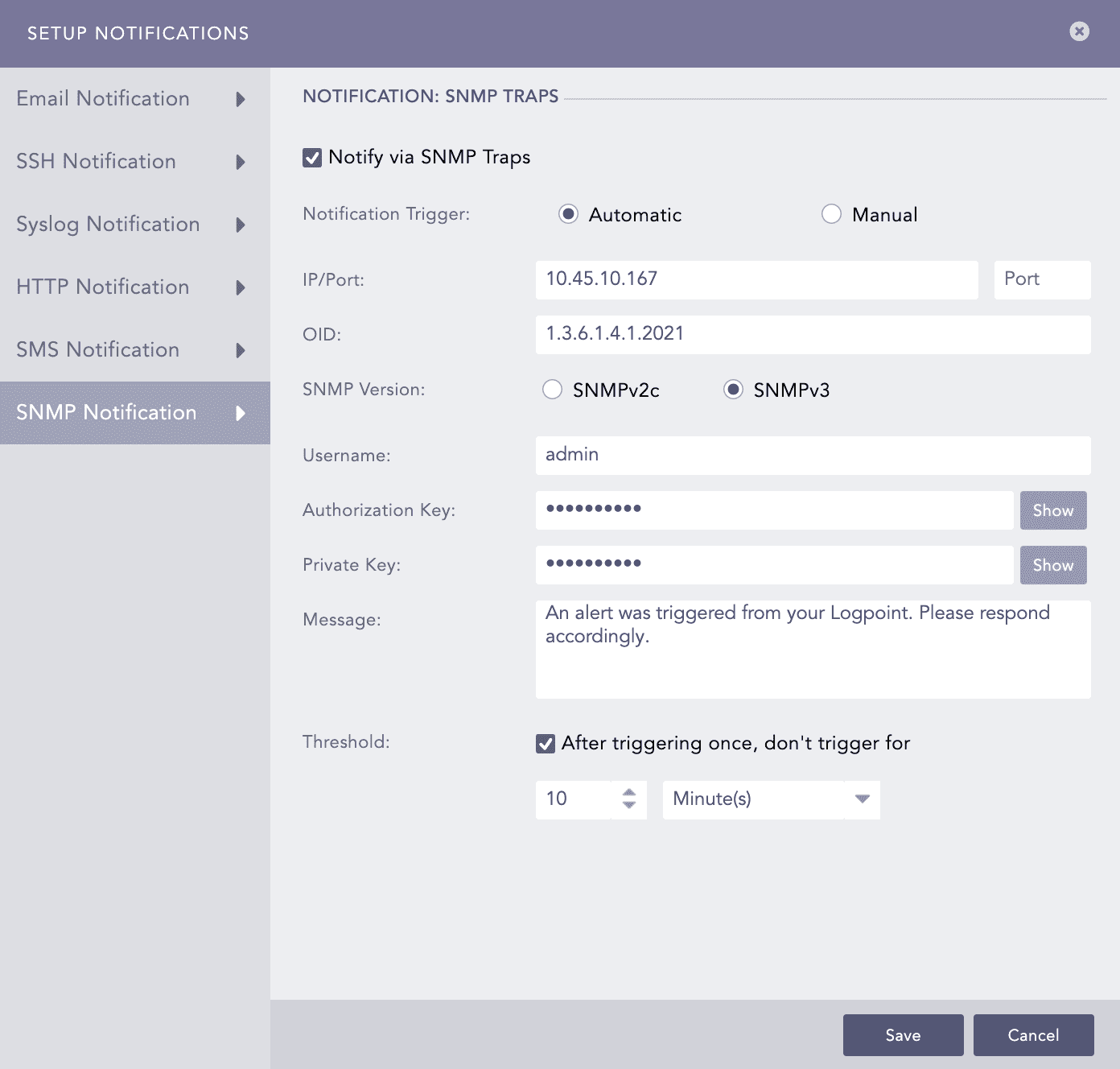
Setting SNMPv3 Configuration¶
Set the Threshold.
Click Save.
We are glad this guide helped.
Please don't include any personal information in your comment
Contact Support