You can use the following types of simple queries to familiarize yourself with the Logpoint Query Language.
Single word search is the most basic search that you can run in Logpoint. Enter a single word in the Query Bar to retrieve the logs containing the word.
login
This query searches for all the logs containing the word login in the message.
Searching with multiple words lets you search the original logs using a combination of words. For searches with multiple words, only the logs containing all the words are displayed.
Note
The order of the words is not important.
account locked
This query searches for all the logs containing both the search terms account and locked in the message.
Phrase Search lets you search the exact phrase in the logs. You must enclose the words inside double-quotes (” “).
Note
The order of the words is important.
"account locked"
This query searches for all the logs containing the exact phrase account locked.
The normalized logs contain information in key-value pairs. You can use these pairs directly in the log search. To see all the logs from the user Bob, use the following query:
user = Bob
This query searches for all the logs from the user Bob.
device_ip = 192.168.2.1
This query searches for all the logs coming from the device with the IP Address 192.168.2.1.
You can combine multiple field value pairs as:
device_ip = 192.168.2.1 sig_id = 10051
You can also combine this with a simple query as:
login device_ip = 192.168.2.1 sig_id = 10051
You can use various keywords to perform logical operations in the Logpoint search query.
Use the logical operator and to search for the slogs containing both the specified parameters.
login and successful
This query searches for all the messages containing the word login and the word successful.
The and operator can also be used for key-value search queries as follows:
login and device_ip=192.168.2.2
Use the logical operator or to search for the logs containing either of the specified parameters.
login or logout
This query searches for all the messages containing either the word login or the word logout.
This operator can also be used with the key-value search query as follows:
device_ip = 192.168.2.1 or device_ip = 127.0.0.1
You can use the hyphen (-) symbol for the logical negation in your searches.
login -Bob
This query searches for the log messages containing the word login but not the word Bob.
-device_ip = 192.168.2.243
This query returns the logs containing all the device_ips except 192.168.2.243.
Note
While searching with field-names, you can also use != and NOT to denote negation.
device_ip != 192.168.2.243
NOT device_ip = 192.168.2.243
By default, the or operator binds stronger than the and operator. When performing the login or logout and MSWinEventLog, Logpoint returns the log messages containing either login or logout with MsWinEventLog.
In Logpoint, the or operator has a higher precedence by default. You can use parentheses to override the default binding behavior when using the logical operators in the search query.
"login failed" or (denied and locked)
This query returns the log messages containing login failed or both denied and locked.
You can use wildcards as replacements for a part of the query string. Use the following characters as wildcards:
? - Replacement for single character.
* - Replacement for multiple characters.
If you want all the log messages containing the word login or logon, use the following:
log?n
Note
This query also searches for the log messages containing other variations such as logan, logbn, and logcn.
log*
This query returns the logs containing the words starting with log such as logpoint, logout, and login.
Note
You can also use Wildcards while forming a search query with field names. To get all the usernames that end in t, use the following.
username = *t
You can use the step function to group fields. To see the log messages with destination_port in steps of 100 as follows:
destination_port |
count |
|---|---|
0 - 100 |
50 |
100 - 200 |
32 |
step(destination_port,100) = 0 | chart count() by destination_port
This query searches for all the log messages containing the field destination_port, and groups them in steps of 100. The value at the end of the query specifies the starting value of the destination_port for grouping.
Note
You can use the step to group using multiple field names.
You can change type-case of your field values. Use the lower function to change the values to lower case. Similarly, use the upper function to change the field values to upper case. The upper and lower functions change the type-case of the values to the same case so that you can observe consistent results.
Use the upper and lower functions with chart and timechart commands.
| chart count() by upper(action)
| timechart count() by lower(action)
The Time Functions extract specied values from a time-based field. The following time functions are supported in the Simple Search Query:
second
minute
hour
day
day of week
month
The arguments taken by these functions are numeric. These functions parse Unix Timestamps.
Note
Unix time is a system for describing instants in time, defined as the number of seconds that have elapsed since 00:00:00 Coordinated Universal Time (UTC), Thursday, 1 January 1970, not counting leap seconds. It is used widely in Unix-like and many other operating systems and file formats.
Example: 1384409898 is the Unix time equivalent of Thu, 14 Nov 2013 06:18:18 GMT
In Logpoint, col_ts and log_ts carry Unix timestamps. However, you can create your own fields which contain the Unix timestamps using the rex or norm commands.
You can use the second function to search for the logs generated or collected in seconds.
The generic syntax for second is:
second(field) = value
The value for second ranges from 0 to 59.
second(log_ts) = 23
This query searches for the logs generated during the twenty third second.
You can use the minute function to search for the logs generated or collected in minutes. The values for the minute range from 0 to 59.
minute(col_ts) = 2
This query searches for the logs generated during the second minute.
minute() can also be used in aggregation functions.
You can use the hour function to search for the logs generated or collected in hours. The values for the hour range from 1 to 24.
Example:
hour(col_ts) = 1
This query displays the logs generated during the first hour.
You can use the day function to search for the logs generated or collected in days.
Example:
day(col_ts) = 4
This query displays the logs of the 4th day.
You can use the day of week function to search the logs for the specific day of the week. The value for day_of_week ranges from 1 (Sunday) to 7 (Saturday).
Example:
day_of_week(col_ts) = 7 OR day_of_week(col_ts) = 1
This query displays the logs in off days, i.e, Saturday and Sunday.
You can use the month function to search the logs generated or collected in months. The value of month ranges from 1 (January) to 12 (December).
Example:
month(col_ts) = 6
This query displays the log activity for June.
Note
You can use the relational operators (>, <, = and !=) with the time commands to create a sensible time-range for your search queries.
The following table summarizes the time functions:
Time functions |
Working Examples |
Value Range |
|---|---|---|
second |
second(cpl_ts) = 20 |
0 - 59 |
minute |
minute(col_ts) = 18 |
0 - 59 |
hour |
hour(col_ts) = 6 |
0 - 23 |
day |
day(col_ts) = 14 |
1 - 31 |
day_of_week |
day_of_week(col_ts) = 5 |
1 - 7 (Sun - Sat) |
month |
month(col_ts) = 11 |
1 - 12 (Jan - Dec) |
You can create a static list with a number of values, and use this list in the search query instead of keying in all the values.
For example, if you create a list EMPLOYEES with the names of all the employees in a company, you can check whether a single user has logged into the system using the following query.
user in EMPLOYEES action=login
The search query matches the value of the field user with all the values in the EMPLOYEES list.
Warning
The name of the list must be provided in uppercase.
You can also use an Inline List while executing a search query.
The generic syntax for inline list is:
field in [value1, value2,....]
which is equivalent to field = value1 OR field = value2.
Example:
source_port in [21, 53, 88, 123]
In cases where the values have multiple words in the inline List, use quotation marks as shown below.
event in ["Process completed", "Process accomplished"]
Tables are external file-formats which contain the information you may choose to associate with a search result. The file formats supported for the tables are CSV, ODBC, LDAP, and Threat Intelligence. The information obtained is prefixed with the table alias in the log messages.
For example:
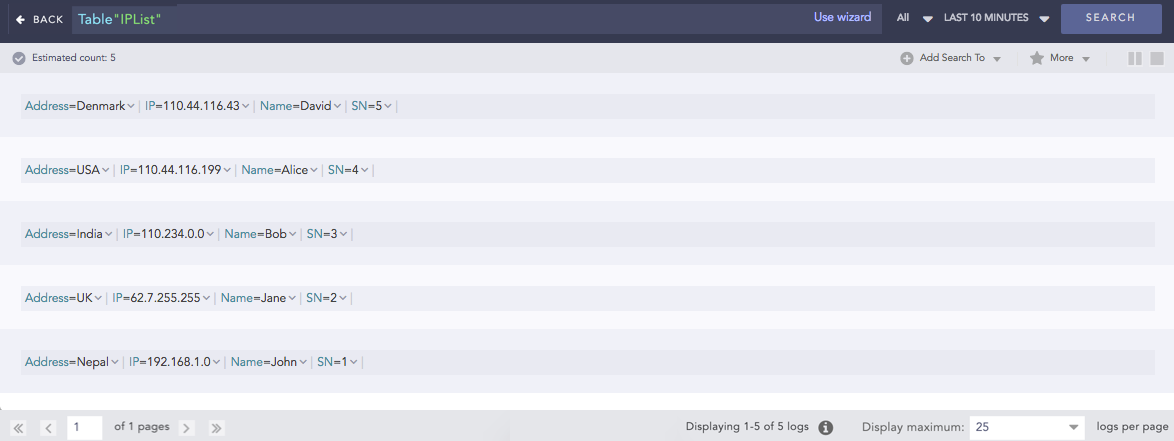
IPList is a CSV table containing fields such as Address, IP, Name, and SN. To view the content of this external CSV table, use the following query:
table "IPList"
The following content is displayed:
To view all student entries in a table called studentResult, which contains student_name, student_roll, and percentage as fields, use:
table "studentResult"
To search for all the student entries in the table studentResult who have passed with distinction:
table "studentResult" percentage >= 80
To search for all the student entries in the table studentResult who have failed:
table "studentResult" percentage < 40
Note
In the Data Privacy Module enabled systems, when you use the table query, you can only see the values of the search results in the encrypted form. You cannot request a decryption for these values.
We are glad this guide helped.
Please don't include any personal information in your comment
Contact Support